computer networks lab manual pdfPc is regarded as the fantastic invention of contemporary era. WLAN & WWAN (Wireless LANs and MANs): These networks are the equivalent of the WAN and LAN in a wireless type. Client-server networks provide centralized backup exactly where data can be stored in a single server. I have never seen such a disfunctional set of network and computer systems as ours. The frequency with which servers, applications, and general systems go down for repair, reboot and servicing is ridiculous. When the programs are up and running the regularly crash on individual PC’s since of inadequacies in our systems.
Any connection to the Net, from a shared 56 K modem to a broadband (DSL, Cable or T1) connection, need to be behind a computer software or hardware-primarily based firewall. If not, this is an quick and gaping hole by means of which crackers can access your private network or use your pc for an attack on a larger public or private network (usually named a DDOS or Distributed Denial of Service attack).
Routers are utilized to connect networks together and route packets of information from 1 network to an additional. Routers, by default break up a broadcast domain, which is the set of all devices on a network segment that hear all broadcasts sent on that segment. Successful monitoring is of utmost value for personal computer network security. It aids in competent management of networks, in which the activity log of routers and varied servers can be closely watched and reported.
Laptop Security Ethics And Privacy introduction to computer networking
computer network development to achieve resource sharingA cable for computer systems is an inevitable factor and is a mandate when you have to use the pc. They can affect the segment visitors amongst networks by filtering data if it does not need to pass. Many wireless sensor networks collect sensitive info. The remote and unattended Operation of sensor nodes increases their exposure to malicious intrusions and attacks. Adhoc network is simple wireless networking that facilitates the connection of two or more computers with just a minimum of specifications. At residence, it lets you share and print files effortlessly.
If you have ever been to a computer lab or if you perform in a cubicle, then you have skilled much more complex networks. This is how thirty computers can use one or two printers. These enable you to save information in central places, rather than just on the hard-drive of your local laptop. They typically use several more wires and can call for a committed network administrator to ensure the wellness and productivity of the network.
Wireless networks LANS give the performance levels allow applications to operate smoothly. For instance, the wireless network LAN customers can simply see e-mail attachments or a massive scale video server of the invisible with information rate up to (54 MBPS). Wireless LAN network can meet only networks with the limits of net applications a residence or office.
The e-mail is not the concern but the delivery mechanism of the threat, which is a Trojan that delivers a rootkit with the finish purpose of joining the laptop to a botnet. Botnets, however, exist in relative obscurity simply because the vast majority of computer customers do not know what botnets are or the threat they pose. The threat of botnets not too long ago resurfaced with renewed media interest attributed to the proliferation of the Stuxnet worm, which took out a nuclear processing plant in Iran and the Dunadup worm, which has infiltrated more than 20 million computers by some estimates.
The network switch operates on the second layer of the OSI standard, known as the “data link layer”. The network switch, as indicated by its name, switches signal paths, so that a message frame goes to a certain location. A switch will improve a networks performance, particularly on networks with several computer systems. A switch has sufficient on-board intelligence to don’t forget the path to each and every location. The network switch handles a message in frames.
When the computers in the sales office crash, or when the finance individuals can’t access their networked spreadsheets, or when the warehouse cannot access the intranet to track a shipment, the business can become paralyzed. A network systems administrator is the particular person who can, and should, resolve these network problems. It’s an critical position.
Security of Information- When data is shared on a network and accidental information loss occurs, information recovery is much more most likely to occur when operating on a network. When shared info is stored on multiple computer systems and databases, it stands to reason that if a tough drive fails, other folks will have the shared information residing in an additional repository. Firewall appliances that are constructed for networks go far beyond what a consumer grade firewall can do.
There are five kinds of systems application, all developed to handle and coordinate the functions of computer hardware. They enable functional interaction amongst hardware, software and humanware. They are: operating systems, device drivers, firmware, programming language translators and utilities. WiFi networks have gained so much reputation in recent instances that it’s hard to picture any other sort of net connection in your residence.
Laptop Aided Engineering introduction to computer networks powerpoint presentation
computer networks a systems approach third edition by larry peterson and bruce davieEthernet is most likely the very best thing that has occurred to computer networks in current years. The advantages of networking are considerable, even on a network of only 3 systems. In pc networking there was by no means a truer statement than that this is a case of benefits seasoned being far higher than the sum of the components. Pc networking is, as a consequence, a rapidly evolving discipline with a lot of fascinating possibilities. Challenges that arise in networking and specifically in the Internet tend to be really global and have the possible to impact upon millions of users.
Software program consists of special management program that controls flow of information between networks. NICs are cards that you put at the back or side of a computer. This allows the computers to communicate with each and every other. A cable is simply a wire that connects the computer systems collectively and the hub is a device that controls site visitors, for example, information that 1 computer sends to one more.
Apart from guarding buyer data, tiny enterprises require to safeguard their economic and organization method info. Installing antivirus application can avoid malicious viruses and Trojan horse programs from attacking your personal computer network. Use anti-spam software to stop spam emails, thereby blocking malicious hyperlinks that could lead to hacker sites.
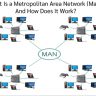
Wide assortment of sources is deployed in WAN. These networks spans not only more than huge domestic location but also internationally. The connectivity of computer systems in branch offices of a corporate organization is an example of WAN. But the greatest WAN on the earth is Internet, a network of several smaller sized networks. Besides World wide web, another massive WAN is Public Switched Phone Network which is converging quick with the Web technologies.
The Web Protocol address is a distinctive number that defines the path for data to attain a distinct personal computer within the operating technique every single program transfers data by means of a distinct port number, assigned. Communication layer is a layer where two computer program can operate and exchange date. Computer systems are connected into a networks to share info and resources. We use net to exchange data or just chat.
No matter how huge or small your organization is, thoughtfully coordinated network infrastructure can aid you reserve your most valuable sources for the explanation you went into business in the first spot. By hiring out IT experts to aid strategy for, set up, and manage your personal computer systems and beneficial information, you are going to be much better equipped to concentrate on bringing your enterprise to the next level, alternatively of worrying about the wires that assist run it.
The main function of the laptop network devices is to forward the information to the appropriate location primarily based on the address that is send along with the data. The two main devices that achieve this are the routers and the switches. The router forwards the data according to the IP address while the switch forwards the data according to the MAC address inside the information frame.
The LAN is a extremely basic type of network where all the units you connect are situated in 1 location. There are two varieties of LAN, peer to peer and client server. A peer to peer network is exactly where two or a lot more computers are connected to each other straight. For example, personal computer 1 is connected to computer 2, computer two is connected to personal computer three and so on. The computer systems are dependent on each and every other so if one unit experiences issues, the other individuals simply will not be capable to connect to each other. The client server variety is where all computers are connected to a main unit. This is far more hassle-free due to the fact if a single pc has difficulties, the other individuals won’t be affected. You will nonetheless be in a position to exchange information.
Discover Pc Network Engineering On the internet computer networks a systems approach third edition
computer networks ppt by forouzanPersonal computer NETWORKING FUNDAMENTALS course introduces students to the ideas and principles of information transmission and pc networks. Formatting the computer is a final resort when all other avenues fail to get Windows unstuck. To set up a fresh operating method, the computer will have to be formatted, which means all private storage will have to go. It can be quite painful to lose all the info on a pc method. Consequently, before you resort to formatting the computer, it is advisable to seek the advice of an experienced laptop engineer or technician to look for an alternative remedy.
The much less your computer has to maintain track of the significantly less time it will take to browse your network or the internet. Windows already takes methods to clean things up for you but this could not be to the extent that you could like. Right here are a couple of methods to take to clean up your laptop so your network or web browsing will be running smooth.
In personal computer network engineering programs, students discover essential abilities and knowledge in a vast assortment of laptop applications, software program applications and troubleshooting methods. Some of the numerous research incorporated in computer network engineering programs are in-depth instruction in Microsoft Windows Network and Desktop operating systems, as well as design, installation and configuration of planet-wide laptop networks, personal computer network wiring, network security, network management, Internet network connections, protocols, webpage hosting and mastering, among other relative topic matter. Students in pc network engineering applications develop crucial pondering, communication and problem resolution skills.
Microsoft Windows 7 is an operating method that is desired by several personal computer customers and owners due to its attributes and simplicity. But some do not dare to install it, because people get in touch with it very tough to keep,” particularly for its updating challenges. To me, it wasn’t a daunting job. The remedy is not tough to find.
This phase involves the physical installation of the neighborhood area network. Cables are run, software program is installed, and computers and other hardware are put in location. In an increasingly connected globe, we’re much more dependent on technologies than we’ve ever been – and that indicates we’re exposed to severe dangers. The very same technology that brings us funny internet sites can also be employed to spy on companies, bring down entire networks and even threaten lives.
Once individuals have their computers networked and connected to the World wide web they neglect to secure their connection. This is specifically essential when you have a wireless World wide web signal. The second generation history of pc program is traceable in between 1959 and 1966. The memory of these computers uses transistors and magnetic tape to retailer information. Transistors supplied more rapidly operations and generate lesser heat. Early version of higher level programming language such as COBOL and FORTRAN have been created at this time.
The job of a network engineer is fairly various from that of a network administrator. Network engineer is responsible for implementing, preserving, supporting and creating communication networks. This kind of job title could also call for an engineer to style communication networks within a organization or amongst firms. The primary target of a network engineer is to ensure a network infrastructure that can increase the overall performance of users. Other job responsibilities of network engineer consist of upgrading system, evaluating vendor products, safety testing, and so forth.
Even though a lot of jobs have been eliminated by advanced technology, new career possibilities have come into existence as companies have increased their dependence on data technology authorities. Networks of laptop hardware and computer software require knowledge in design and style, building, implementation, and maintenance in order to stay operational. In addition, company administrators and corporate executives must recognize how technologies can be applied to real world company troubles if they hope to benefit from a lot more efficient systems. People who are willing to advance their understanding of information technologies will discover that there are numerous higher paying career opportunities offered.