Do you work with a team that deals with cybersecurity? If yes, then you are not alone. Cybersecurity is one of the fastest-growing fields in today’s world. Many companies have come to rely on the security of their organization and this has only increased in the past few years. This has led to increasing demand for professionals with cybersecurity skills. However, this has also led to a great deal of cybersecurity fraud and unscrupulous companies posing as legitimate businesses. This has made the field even more rewarding for those that seek to take advantage of it. To help you understand the various levels of cybersecurity compliance, we have detailed the different levels of CMMC compliance below.
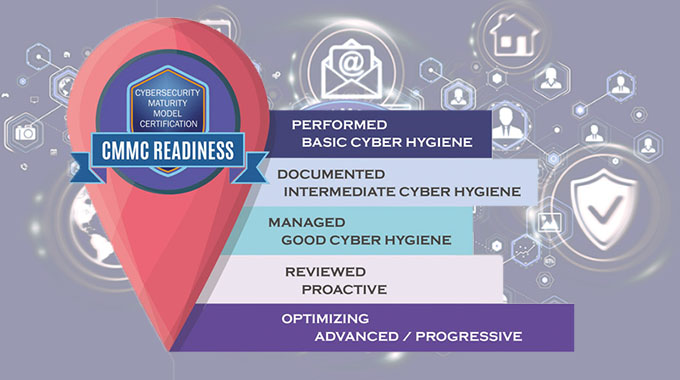
What Are the Different Levels of Cybersecurity Maturity Model Certification (CMMC) Compliance?
The Cybersecurity Maturity Model Certification (CMMC) assists organizations in verifying the cyber hygiene of their business partners. It is a model that summarizes the state of cybersecurity maturity for a given organization based on the organization’s compliance with the PCI DSS standards. This certification is offered by a third-party organization, and the organization that receives this certification is deemed to be compliant with the PCI DSS standards. However, unlike an ISO standard, this model remains proprietary and is protected by copyright laws.
Baseline Cybersecurity compliance
This is the lowest level of compliance and includes only the bare minimum of cybersecurity best practices. The organization is granted this level of compliance if they have implemented only a few key standards. Examples of the standards that are found at this level of compliance include ensuring the use of a firewall, ensuring the use of a virus protection software, and making certain organizational policies. Moreover, the organization is only granted rudimentary disclosure requirements with regard to its security policies. This level of compliance also includes penetration testing and vulnerability assessments. However, the organization should note that it is not expected to carry out any ongoing assessment of its cybersecurity risks. This is because the most important aspect of cybersecurity is risk management.
Business-to-Business (B2B) Cybersecurity compliance
This level of compliance involves certain standards and requirements that are only relevant to the buying and selling of goods and services. Examples of standards and requirements that fall under this level of compliance include the use of encryption, being compliant with the EMV standards, and being compliant with the FedRAMP standards. Moreover, the organization must also have adequate policies and procedures in place for the handling and handling of sensitive data. This level of compliance also includes B2B security best practices such as an ongoing assessment of risk, an assessment of the overall cybersecurity environment, and the creation of a B2B security plan. However, the organization should note that at this level of compliance, the business does not have to actively protect itself against threats.
B2B compliance with an added layer of personal security
This is the next level of compliance that involves making certain adjustments to the existing standards and requirements to include the protection of the public and private data of the business partners. The standards that are included under this level are the same as the ones that are found at the level of compliance above. However, there is an added layer of protection that involves the implementation of additional standards such as those that are related to data loss prevention. The implementation of this level of compliance requires the implementation of risk assessments, ongoing assessments of risk, and ongoing risk management. Moreover, this level of compliance also requires the implementation of an authentication and authorization management solution.
Personal Security and Automation layer
This is the most advanced level of compliance and includes best practices that are relevant to the protection of the sensitive data of individual customers. The standards that fall under this level of compliance include the protection of the sensitive data of the customers, the use of multi-factor authentication, and the use of encryption. Moreover, the organization must be compliant with the PCI DSS requirements related to threat awareness. This level of compliance also includes the use of continuous monitoring and scanning, a threat assessment, report generation, threat hunting, and a threat response plan. It is also important to note that the organization must be compliant with the requirement to actively protect itself against threats.